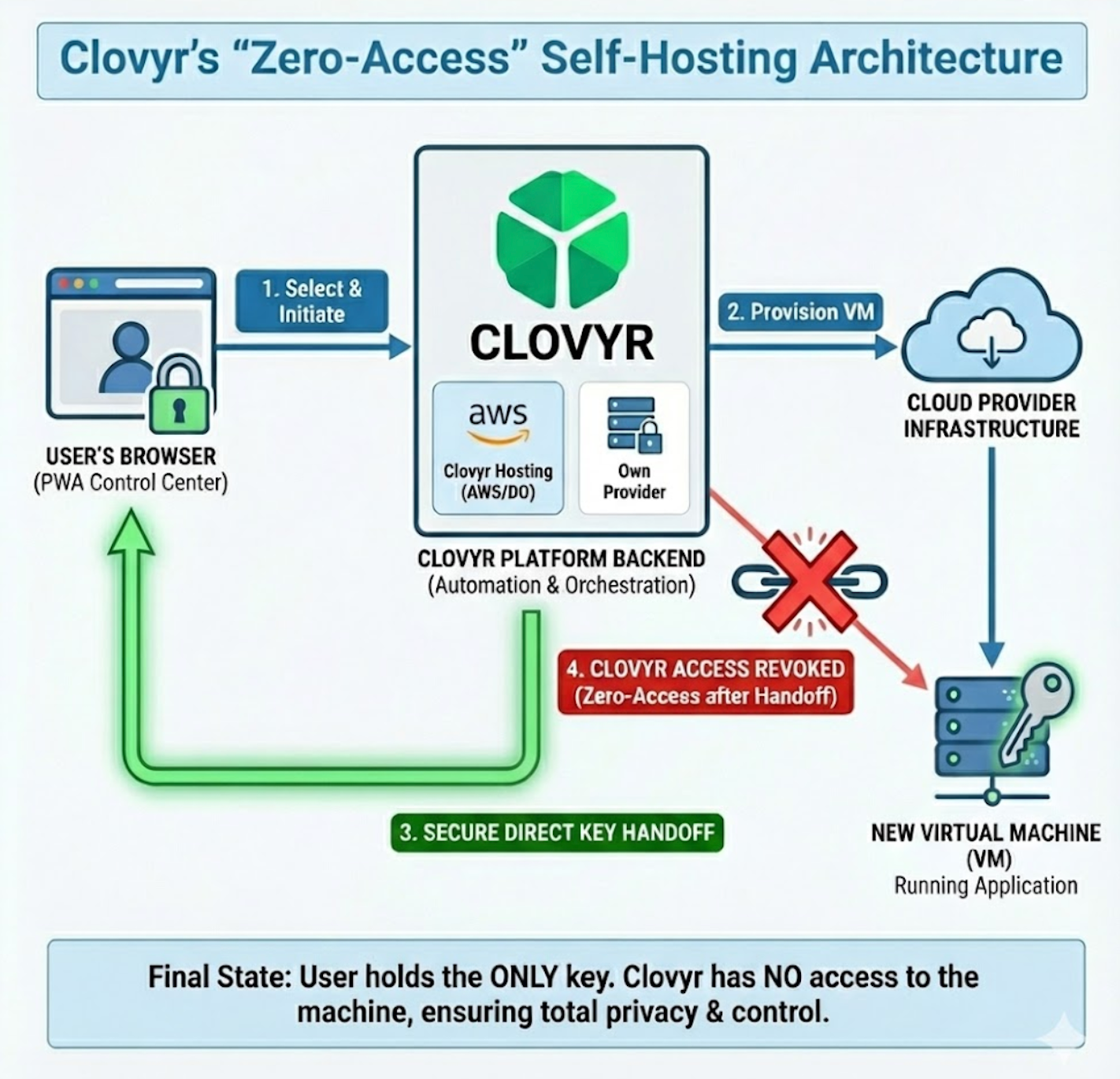
Clovyr's Self-Hosting Architecture: Private & Secure Application Deployment
Clovyr simplifies the process of self-hosting applications through a Progressive Web App (PWA), offering a unique architecture that prioritizes user privacy and control. Unlike traditional managed hosting, Clovyr's "zero-access" approach ensures that once your server is up and running, only you hold the keys.
How It Works: A Step-by-Step Breakdown
- User Access via PWA: You begin by accessing the Clovyr platform through a Progressive Web App directly in your web browser. This acts as your control center.
- Provider Selection: You choose where you want your application to run. You can select Clovyr managed hosting (which utilizes infrastructure from providers like AWS or DigitalOcean) or connect your own existing cloud provider account.
- VM Provisioning: Clovyr's backend automation communicates with your chosen provider to provision a new, dedicated Virtual Machine (VM) tailored for your application.
- SECURE KEY HANDOFF (The Crucial Step): This is where Clovyr differs. As the VM is created, a cryptographic root key (the master "password" for the machine) is generated. Instead of Clovyr storing this key, it is securely and directly transferred to your browser.
- Total User Control: Once your browser receives the root key, Clovyr's systems immediately lose all access to your VM. You now have sole, direct ownership and control over the machine and the applications running on it.
The "Zero-Access" Advantage
The defining feature of this architecture is the secure, direct-to-browser key transfer. This diagram illustrates the flow, showing how the Clovyr platform facilitates the setup but ultimately steps out of the loop, leaving a direct, secure connection between you (your browser) and your server.
This approach provides the convenience of a managed service—automated setup and easy deployment—without sacrificing the privacy and security benefits of true self-hosting. Your data and applications remain completely under your control, inaccessible even to the platform that helped you set them up.